This is the second in a series of walkthroughs for the Thunderdome multi-cloud Cyber Range from Pwned Labs. This post will guide you through capturing the second flag, "Pulled From the Sky". In the process, I will cover various tools and techniques, illustrating that there are multiple ways to achieve an objective.
Beginners can benefit from replicating this tradecraft, and even pros might learn a new thing or two! Walkthroughs also give me the opportunity to solidify and refresh my own understanding of offensive security concepts.
This walkthrough follows on from flag 1 - Emerge Through the Breach. Let’s recap what we did to capture flag 1:

In the writeup for flag 1, I gave a little hint of what to expect for flag 2:
Make a note of the above, it's a snapshot (ahem) of what you'll need for the next flag!
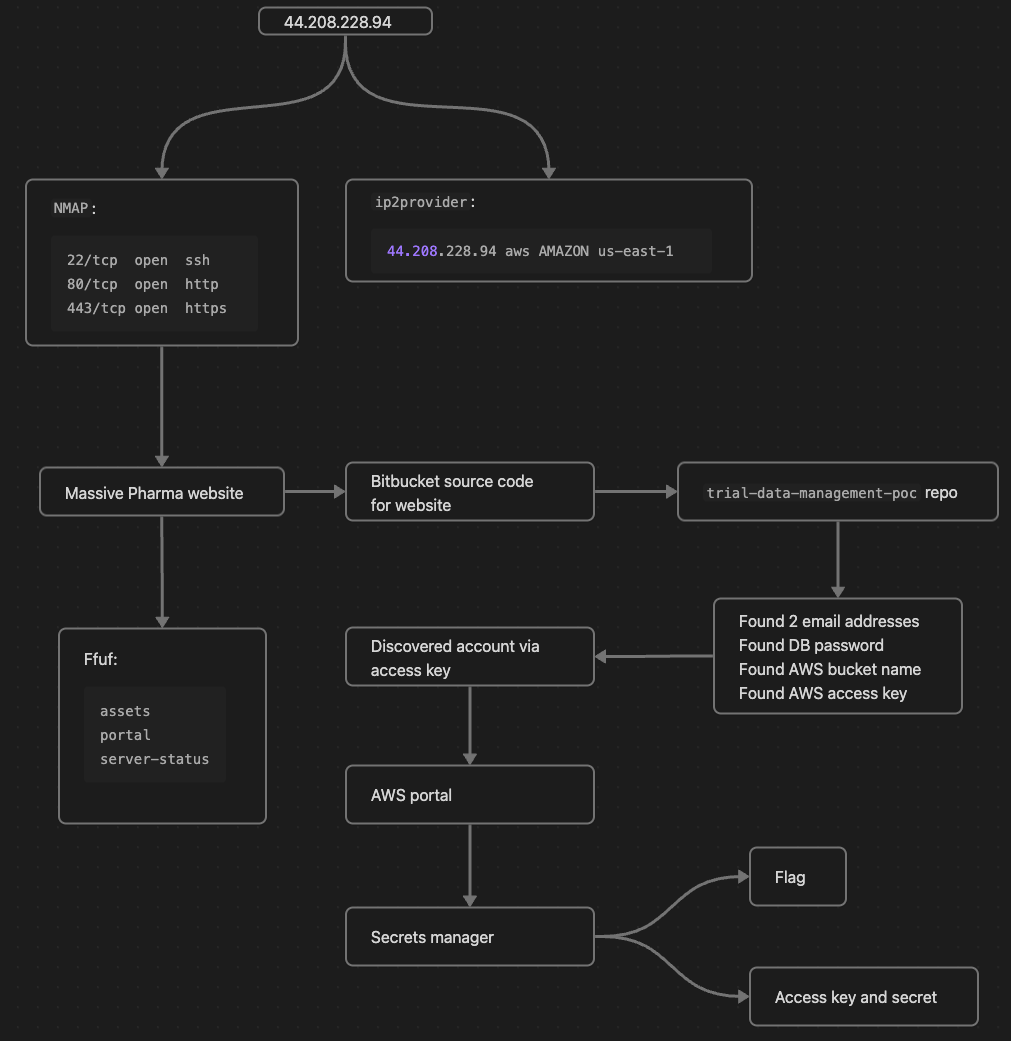
If you didn’t guess, we will be grabbing the snapshot arn:aws:ec2:us-east-1:211125382880:snapshot/snap-0c241b0d00d234853 which was discovered by our CloudFox enumeration and examining it locally. Here is the CloudFox inventory again to remind you:

When I was going through the inventory it wasn’t obvious that the next step to finding flag 2 would be the snapshot (although I had a strong suspicion). Let’s have a look at what CloudFox collected in the loot directory:
CloudFox suggested some steps which could be taken to attempt Remote Code Execution on the EC2 instances that were discovered - instance/i-0874ad63d9693239c and instance/i-0d67cb27d5cc12605. Let’s cat instances-ec2InstanceConnectCommands.txt and see what it says:
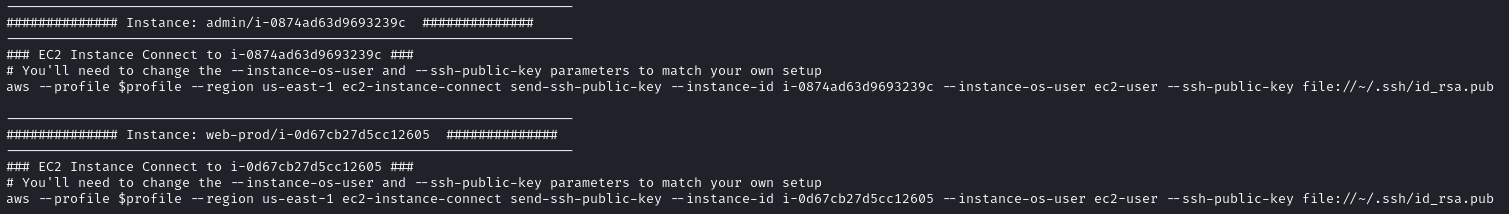
The first instance listed is admin/i-0874ad63d9693239c. We’ll ignore that as it’s out-of-scope, and look at web-prod/i-0d67cb27d5cc12605. Note what the requirements are to connect to web-prod :
You'll need to change the --instance-os-user and --ssh-public-key parameters to match your own setup.
We see an AWS CLI command leveraging ec2-instance-connect - more information here - https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/connect-linux-inst-eic.html. This is a simplified way to connect to EC2 instances without having to distribute ssh keys. It temporarily pushes your ssh public key to an EC2 instance, allowing you establish an ssh session. The user trying to do this needs to have the relevant permissions and the EC2 instance needs an appropriate attached role. Here’s the command CloudFox says we should run: